In late October 2025, a highly sophisticated social engineering attack targeted representatives of Armenian media and civil society. This multi-stage scam leveraged fake WhatsApp (and in some rare cases, Viber) accounts of prominent individuals, utilizing hacked Armenian phone numbers to establish credibility.
The attack unfolds in a series of carefully orchestrated steps:
1. Impersonation and Initial Contact: Attackers initiate contact with the target from a fake WhatsApp account, pretending to be a well-known professional from the same field. The editor of Armenian media outlet 168 Hours reported on her Facebook account that her name was used in fake accounts targeting other journalists and editors.
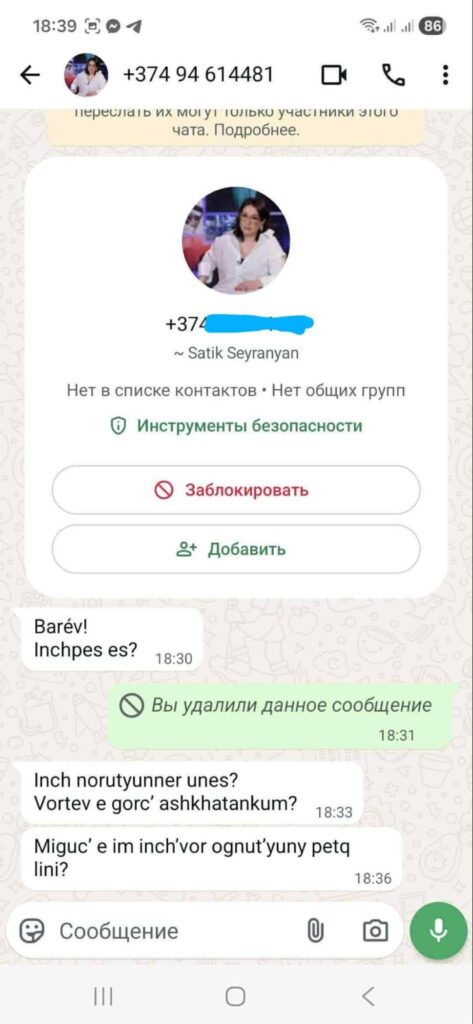
2. Building Rapport with AI Assistance: The imposter begins a conversation in Armenian, though in some instances, it’s evident that AI translation is being used due to non-native phrasing in some rare cases. What’s clear is the extensive research undertaken by the attackers into the target’s personal and professional relationships.
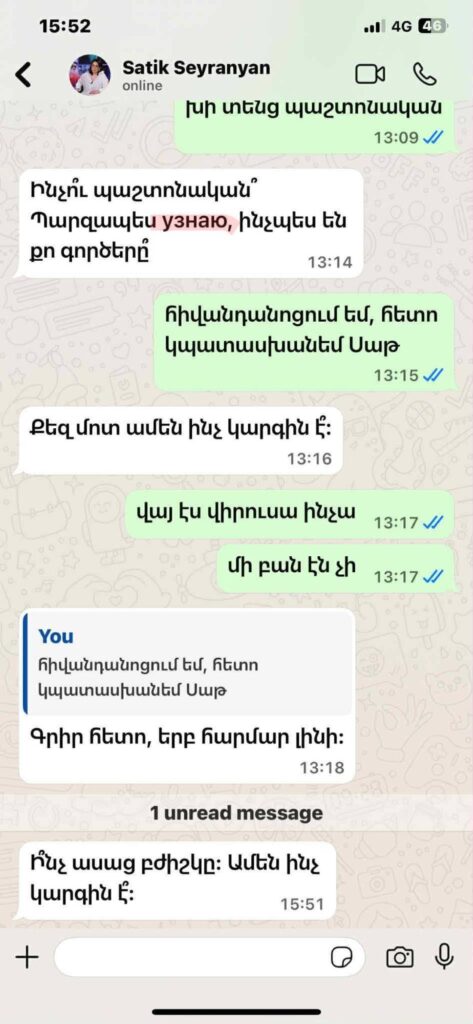
3. The “National Security Service” Deception: The fake contact first claims to have a new mobile number. After a few messages about life and work, they inform the target that they’ve become a victim of forgery, with criminals from Azerbaijan allegedly transferring millions of dollars into their bank account. The imposter then states that the National Security Service (NSS) is investigating the matter. After instilling fear of national betrayal prosecution, the fake actor calms the situation, assuring the target that the NSS views them as honest and patriotic and expects their collaboration.
4. The “Joint Operation” Call: A second individual then calls, posing as an NSS officer. This person speaks in Russian, explaining that it’s a joint operation between Armenia and Azerbaijan, requiring all communications to be recorded in Russian as a common language.
5. The “Safe Account” Ploy: The fake NSS officer then instructs the target to transfer all their money from their personal bank accounts to a “special NSS account” to separate it from the alleged criminal funds.
Fortunately, all targeted individuals in this tracked operation realized something was amiss at this final stage or earlier, either independently or after being informed by CyberHUB staff and social media.
This attack suggests a highly organized group with significant resources dedicated to preparation. It’s particularly noteworthy that the targets are journalists and civil society members, rather than financially prominent groups, raising questions about the true motives behind such a substantial investment of time and human resources.
Our hypothesis is that beyond financial theft, targeted individuals could potentially become victims of blackmail or be coerced into committing illegal acts. We believe that foreign state backed actors can operate in this manner.