In early March 2025, CyberHUB-AM identified a targeted spear phishing campaign focused on individuals and organizations within Armenia’s civil society and public sector. The campaign exhibited IOCs consistent with advanced persistent threat (APT) operations and has been attributed to UNC5792, a group previously identified by Mandiant.
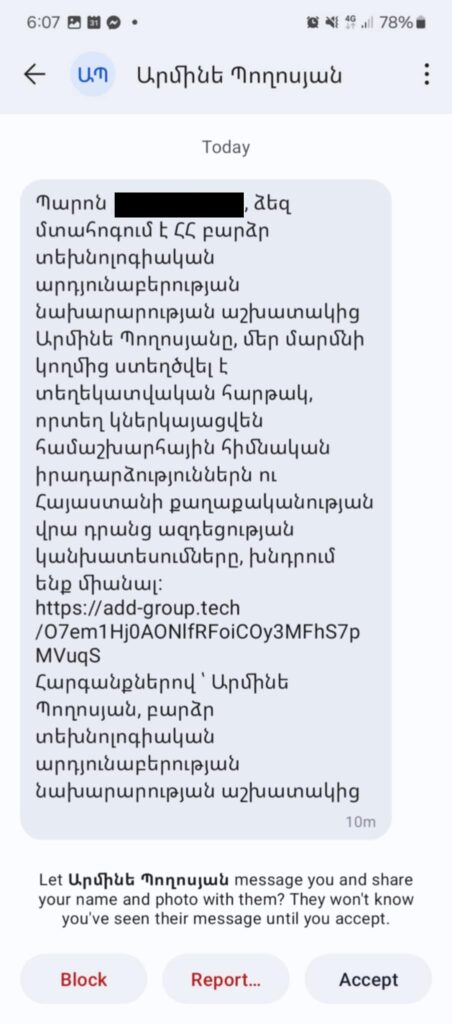
The attackers impersonated an imaginary “Armine Poghosyan”, who is supposedly “an employee” of Armenia’s High-Tech Industry Ministry, using Signal to send messages inviting recipients to a purported “information platform” on global and Armenian political events. The core of the attack involves highly malicious, temporary URLs (initially on add-group.tech, then shifting to group-add.com), which are designed to compromise the targets; notably, the attackers demonstrated real-time adaptability by providing a new, active malicious link on a different domain immediately after being informed that the initial URL had expired.
Target Profile
The threat actor targeted individuals classified as high-value, including:
-
NGO operating in the public interest – active in the field of legislative reform and election monitoring
-
Security Analyst — An individual involved in national-level policy and political analysis
-
Armenian Electoral Commission — Government institution
-
Target Sectors: Non-profit, civil society, and government institutions
These targets suggest an intent to collect intelligence or exert influence within Armenian public affairs.
Attack Methodology
The phishing attempt was delivered via the Signal messaging platform, deviating from traditional email-based vectors and reflecting a shift toward secure, encrypted platforms for social engineering operations.
-
Impersonation: The attacker posed as “Armine Poghosyan,” allegedly representing the Ministry of High-Technological Industry of Armenia.
-
Lure: Recipients were invited to join a newly formed “information platform” described as providing strategic forecasts on global events and their impact on Armenian politics—an offer that was contextually relevant and designed to establish trust.
Malicious Infrastructure
Three domains were observed as part of the infrastructure:
-
Initial Domain:
-
add-group.tech -
URL:
hxxps:[//]add-group.tech/O7em1Hj0AONIfRFoIC0y3MFhS7pMVUqS
-
-
Secondary Domain (Following Detection):
-
group-add.com -
URL:
hxxps:[//]group-add.com/kPDOT4Wr7PrKmkQtK6LrhFxmmo6LA7EE
-
-
Third Domain (a second target):
-
signal-groups-add.com -
URL:
hxxps:[//]group-add.com/kPDOT4Wr7PrKmkQtK6LrhFxmmo6LA7EE
-
All 3 domains were assessed as malicious with high severity by VirusTotal and supported by intelligence from Mandiant and Google Threat Intelligence. All 3 were attributed by Mandient to UNC5792.
Notably, these URLs were temporary in nature. Attempts to analyze the links in a controlled environment by CyberHUB-AM revealed that the original URL had already expired, indicating that the threat actor employed infrastructure designed for short-lived accessibility, reducing the window of opportunity for defenders to respond.
Adversary Adaptability
The incident also demonstrated real-time adaptability. When a targeted user—under the observation of investigators—informed the attacker that the original link had expired, a new, functioning URL was immediately provided. This behavior confirms that the attacker was actively monitoring communication and managing the phishing infrastructure in an agile manner.
These actions suggest:
-
A high level of attacker engagement
-
Operational flexibility
-
Intent to sustain access until successful delivery of the payload