A sophisticated spearphishing campaign was identified targeting dozens of NGOs in Armenia on April 8th, 2025. The attackers impersonated Vassilis Maragos, the EU Ambassador and Head of Delegation in Armenia, initiating contact through Signal messenger.
EU Delegation to Armenia was immediately notified about the phishing attempt and evidently this case was not interconnected with any of the EU systems. Some of the representatives of the Armenian Civil society contacted EU Delegation as they found the message unusual and suspicious. Thanks to the warning of the CSO members the attack attempt was not successful.
The Attack
The phishing message, disguised as an invitation to a video conference titled “EU-Armenia Cooperation: Opportunities and Challenges for Civil Society,” aimed to trick recipients into believing they were being invited to a legitimate event. The message specified that the video conference would take place on April 28th at 10:00 AM on the Microsoft Teams Video platform. Victims were instructed to agree to participate, upon which they would be registered.
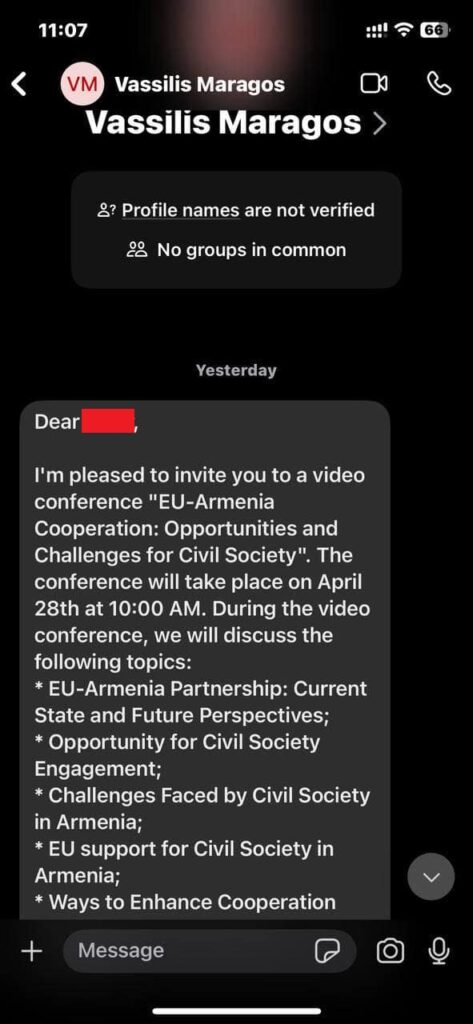
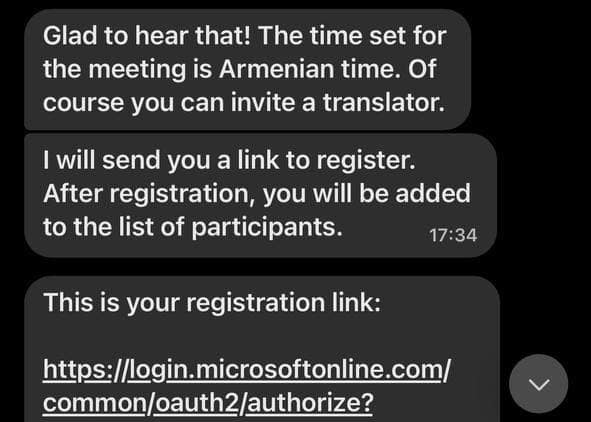
The phishing attempt involved a malicious URL disguised as a Microsoft Teams meeting link. The message contained a link from a legitimate Microsoft login page. Once the targeted individual successfully logged in, the process would redirect to a separate browser window containing a Microsoft authentication token. The crucial step for the attackers was then to instruct the targeted individual to copy and paste this new link (containing the authentication token) and send it back to the attacker via Signal. This action would then trigger a Microsoft Entra ID device joining process on the victim’s account.
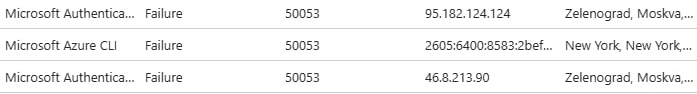
The attackers were able to successfully compromise at least one account belonging to a key Civil Society Organization (CSO) leader. The CyberHUB-AM team, working with the CSO’s IT manager, provided incident response. During this process, they observed how the attackers successfully enrolled into the CSO leader’s Microsoft Entra ID and tried to access it via Microsoft Azure CLI. The connections originated from the IP addresses: 95.182.124.124, 46.8.213.90, 188.130.142.95 all of which were identified as belonging to the cloud server provider Biterika Group LLC, based in Russia.
When the initial attack was thwarted by the incident response team, the attackers demonstrated significant persistence. They re-established contact via Signal, providing another link and instructing the victim to go through the procedure again. The attacker claimed, “I clarified, you did everything right, but for some reason it didn’t work. You’ll have to do the same thing again and IT will fix it,” attempting to re-engage the victim and regain access.
Relation to Veloxity Reports: This incident strongly correlates with the advanced persistent threat (APT) activities and techniques detailed in recent Veloxity reports, particularly “Phishing for Codes: Russian Threat Actors Target Microsoft 365 OAuth Workflows” (April 22, 2025) and “Multiple Russian Threat Actors Targeting Microsoft Device Code Authentication” (February 13, 2025).