This report details a phishing campaign targeting Telegram users in Armenia, aiming to gain access to their accounts.
Attack Vector
The attack begins with unsolicited messages forwarded by already hijacked Telegram accounts to their contacts in Armenian. The attacker claims to be participating in a contest and requests the user’s vote, providing a malicious obvuscated URL, displayed as hxxps[://]DAXCEARM[.]WVE.
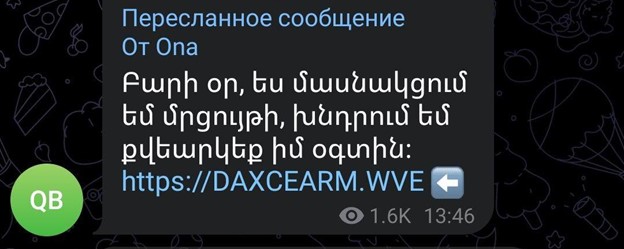
The actual URL, however, is this one: hxxps[://]cutt[.]ly/Hw2lLLHa. It is a shortened URL, using the service https://cutt.ly/, which has increasingly been used in phishing attacks in Armenia. Upon loading, the short URL will redirect to a Telegram hijack page, which in the initial stages of the attack surprisingly was in the Uzbek language: hxxps[://]dolbaebshesp[.]in/.
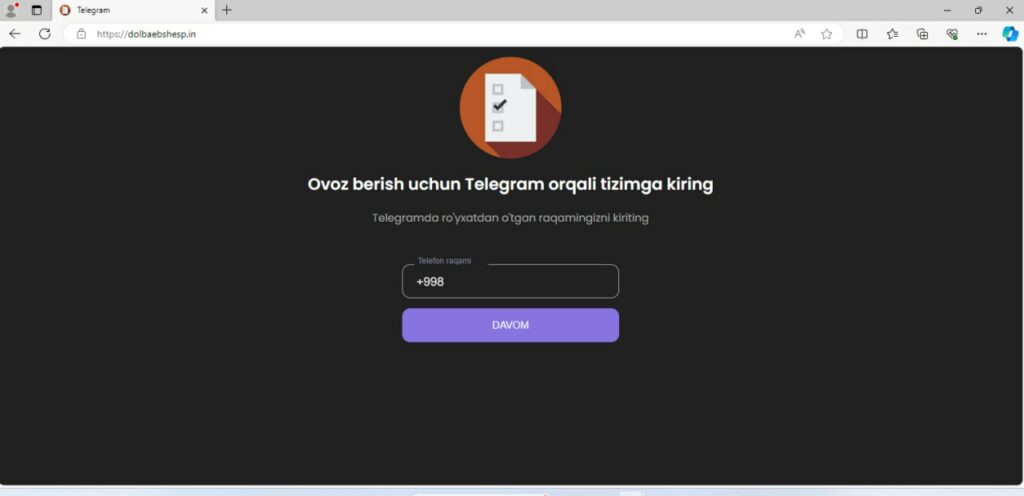
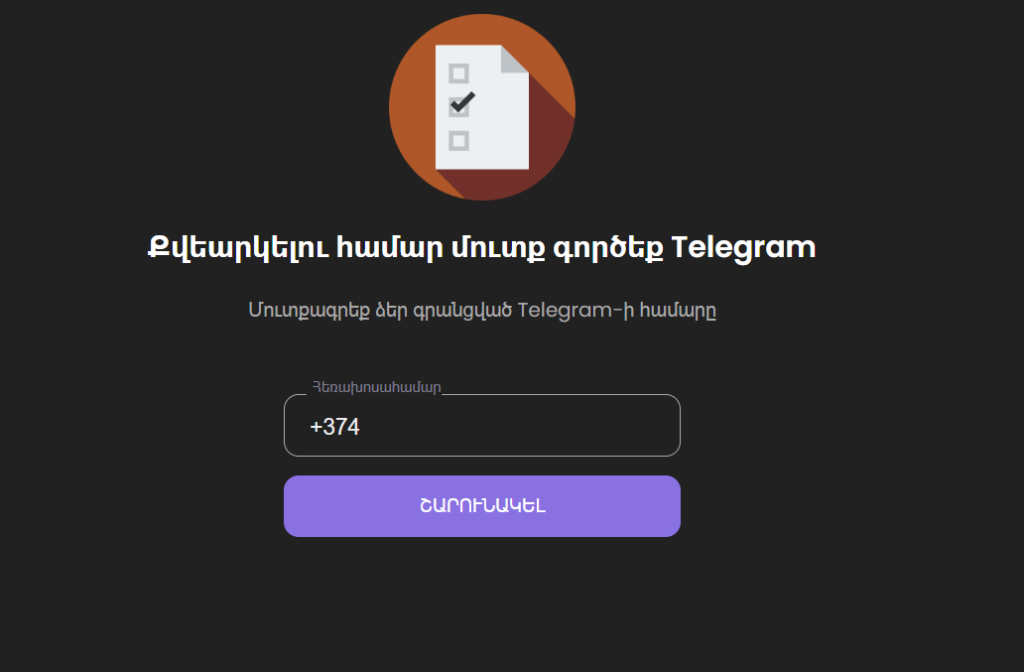
At a later stages of the attack the URL started rending an Armenian version of the fake login page.
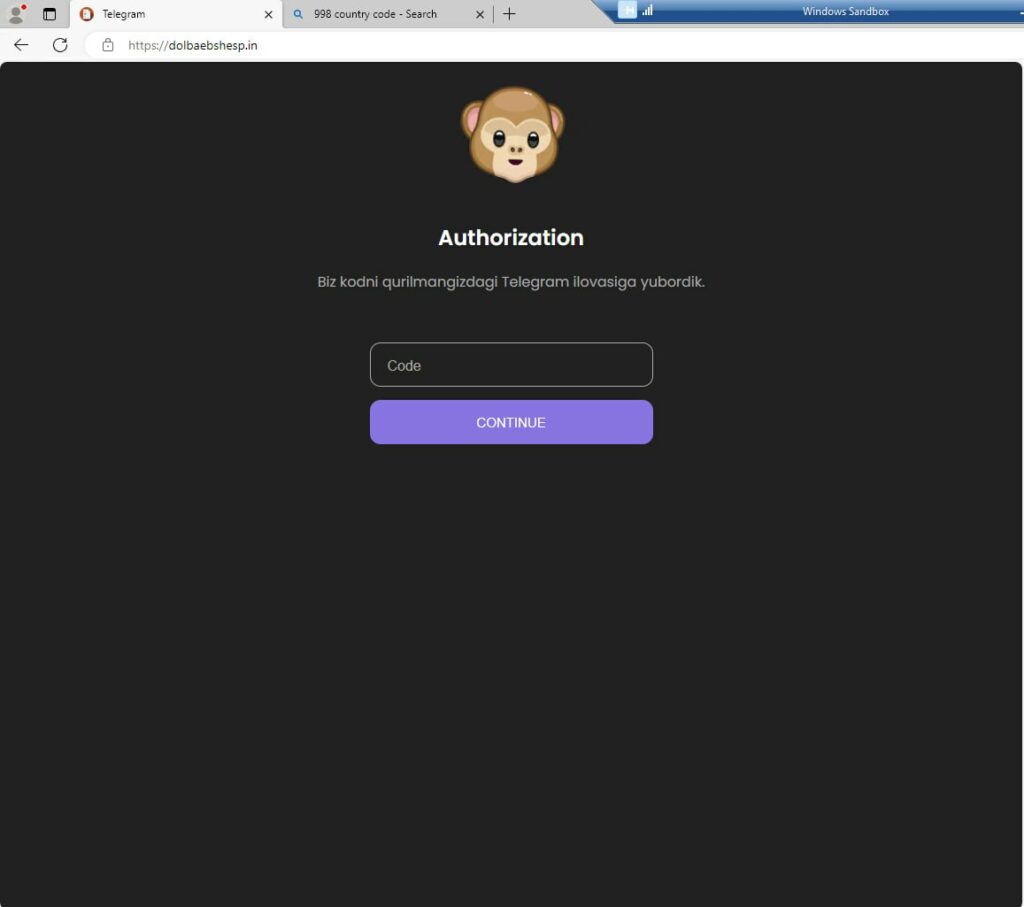
When the user submits their phone number, they are presented with a screen requesting a security code, mimicking the legitimate Telegram login process.
If the attack is successful, a new authenticated session appears in the victim’s Telegram account under the “Devices” section.
The attackers can then use this access to send similar messages to the victim’s contacts, propagating the attack further.