Executive Summary
Threat-researchers at CyberHUB-AM, with the support from Internews’ Martijn Grooten, are tracking a Remote Access Trojan targeting the Armenia International Airports and Armenian State Bodies. The attack was first identified by a Singapore-based cybersecurity researcher Zhixiang Hao.
The malware is embedded within an MS Word document, which is presented as an official warning message from Armenia’s National Security Service regarding state secrets, and employs VBA Macro code and powershell script to install a Remote Access Trojan.
In a different but related campaign, people in Armenia supporting those in Nagorno-Karabakh were targeted with a different information stealing malware, although the version we analyzed was non-functioning.
The landlocked mountainous region of Nagorno-Karabakh has been the subject of a long-standing territorial dispute between Azerbaijan, in which it lies, and its ethnic Armenian majority, backed by neighboring Armenia. Internationally recognized as part of Azerbaijan, until recently much of it was governed by the unrecognized Nagorno-Karabakh Republic, also known as the Republic of Artsakh.
This report provides an in-depth analysis of both malware samples, their functionality, and associated indicators of compromise (IOCs) to enable effective threat mitigation. It also provides some local context helpful to understanding this campaign.
Targeting Data
According to VirusTotal, a file haytararutyun.doc (‘haytararutyun’ means ‘announcement’ in Armenian) was sent as an email attachment. The email was sent from the address [email protected] The domain aacpress.net is no longer resolving, but was registered on 8 September, a few days before the email was sent. The domain is likely made to appear like it belongs to the Armenian acronym of the National Security Service (Azgayin Anvtangutyan Carayutyun – AAC). The body of the email contains a short warning in Armenian: “Please take this into consideration!!!” and the malicious MS Word file as attachment.
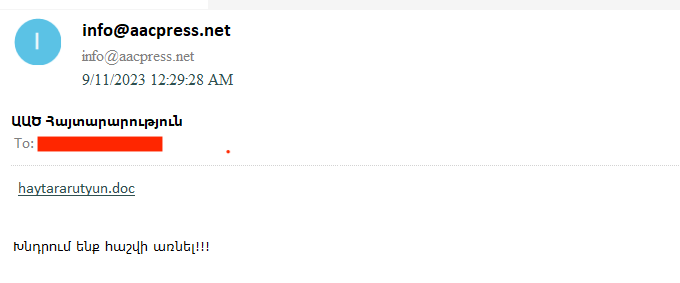
The recipient of the email uploaded to VirusTotal and thus likely the target of the campaign is someone with a @aia-zvartnots.aero email address. The domain name aia-zvartnots.aero is used by Armenia’s main international airport, also known as “Zvartnots”, as can be seen in their contact forms.
![]()
===
Attack Overview
The email was sent on 11 September 2023 and aside from a short text, included a Word doc attachment named haytararutyun.doc, which means ‘announcement’ in Armenian. The document is written in fluent Armenian, except for incorrect use of punctuation marks. It is possible it was created using an online translation service. It is extremely rare for malware targeting Armenians to be written in Armenian.

The text in the attachment translates to:
To the State Organizations of Armenia
Dear citizens,
Our country is facing the danger of a new war. Please try to be united in this difficult moment and do not reveal secrets to the enemy. Instructions have been sent to you regarding preventive measures in the classified area. Please activate the “Enable Content” button to view the full text.
Decision No. 498-L on approving the service implementation and development program and the 2021-2023 plan-schedule of measures ensuring its implementation was provided to you on 04.14.2021. No. 03/01852-2021 in execution.
It is necessary to submit information to the regional governor’s office on the activities provided for in points 2.3, 3, 4, 6 of Annex 2, approved by the above-mentioned decision, by February 1
REPUBLIC OF ARMENIA
NATIONAL SECURITY SERVICE
In older versions of Word, should the recipient decide to enable macros, VBA code embedded in the document is executed. In this code, there is a PowerShell command that downloads the file ekeng-mta.exe from a remote server hxxps[://]karabakhtelekom[.]com/api/ekeng-mta[.]exe
A few things are worth noting here. First, the PowerShell code isn’t obfuscated in the document and can be found by simply running the strings command. This is quite unusual for modern malware, which tends to use obfuscation.
The domain karabakhtelekom[.]com was registered on 4 September and when the email was sent, it pointed to the IP address 141.136.33[.]28. This IP address belongs to a shared host at Lithuanian hosting provider Hostinger. Interestingly, the A record of the domain aacpress[.]net, used to send the email, pointed to the same IP address. Both domains have since stopped resolving.
Finally, ‘ekeng’ is the Armenian agency for e-government services.
The ekeng-mta.exe executable again calls some PowerShell code. This code, base64-encoded in the executable, downloads and executes yet another PowerShell script from hxxp://139.84.231[.]199:8080/get/j6F2fQnRO4/mta.ps1
The server 139.84.231[.]199 is hosted in South Africa and has no recorded history beyond this campaign.
The powershell script mta.ps1 downloads another file from the same server: hxxp://139.84.231[.]199:8080/get/CF6frm57nj/mta.dll and then uses the open source UrbanBishop tool to execute it.
The file mta.dll is detected by the Triage sandbox as being a version of the AsyncRAT remote access trojan. AsyncRAT is an open source RAT and has significant code overlap with other RATs, so that it may well be another RAT being used here.
Attribution and history
The Word document is written by a user ‘Galilei’. Interestingly, this name also appears as the Windows user in a debug path of mta.dll, strongly suggesting the same person created the malicious document and compiled the DLL file.
The Word file was created on 11 September and while such dates may be forged, it is less than an hour before the email was sent, strongly suggesting the date is correct. The DLL file has an obviously forged creation date in 2048, but was digitally signed on 14 August 2023, which may be the real creation date. The signature date of the ekeng-mta.exe file is 19 July 2023, while the (possibly forged) creation date is 26 August 2023.
More interesting is the fact that both files were first submitted to VirusTotal on 30 August, with the DLL submitted twice on that date. VirusTotal telemetry suggests the three submissions were different and one of the submissions is from Armenia. This strongly suggests the same malware had been used in a previous campaign on that day. No further details of this campaign are known.
Second campaign
Among other domains hosted on 141.136.33[.]28, one stands out: nkrmil[.]com. Opening this domain in a web browser redirects to nkrmil[.]am, the official website of the Ministry of Defense of the now dissolved Republic Artsakh.
However, we did receive an email that was sent to someone active within the 120k Project, an initiative that aims to draw the world’s attention to the situation in Artsakh. The email body consisted of short message in Armenian about leaked data and a link:
hxxps://nkrmil[.]com/resources/AAC_Haytararutyun.exe
This link didn’t redirect to nkrmil[.]am, but to a Windows executable file with sha256 hash 5c8a10179264f69525e7169566a03474c922a72f7fc5e9704a6e7a2c166887bf.
Running the file in a sandbox didn’t show any activity beyond some simple Windows commands. Thankfully, analysis of the file was easy, as it’s written in .NET and could be turned into readable code using the ILSpy tool. This explained the lack of activity in the Sandbox, as the code would have exited upon reaching Environment.Exit(0).
It is possible that a development version of the file (which also writes “Hello World!!” to the console) was sent, perhaps by accident, or perhaps by someone who wanted to reach their KPI.
The rest of the code suggests that this was meant to be an infostealer, with Telegram used as a channel for data exfiltration and GitHub used as a secondary channel. That is not uncommon in modern malware.
The debug path present in the executable contained a name different from ‘Galilei’. This name happens to be a fairly unique name of someone listing themselves on LinkedIn as a trainee at the Azerbaijan CyberSecurity Center.
Interestingly, looking on other files on VirusTotal with this particular name helped us find two related files: e0c9f855f45de79033017b97cb8c7d8832ab12a31dd522af7106d320d2b490f0 and 5bc6c257e41b3709d74ae8e6dc9300ae21ab96ef668dcaf368cf119e836b4ead.
The former file was uploaded from the United States on 19 September, the same day the email was sent to the 120k project. It is possible that it was sent to a different person. It fails to run for the same reason as the original sample.
The third file is more basic and doesn’t contain all the functionality of the other samples, suggesting this was an earlier development function. It was uploaded to VirusTotal a day earlier, perhaps unsurprisingly from Azerbaijan.
About Attackers
What are our conclusions about attackers:
- Most probably attacks were implemented by the Azerbaijani hackers.
- The attack is not very sophisticated from the technical perspective, however, the attackers are very well informed about the Armenian governmental structure, processes, and institutions.
Malware Sample Information:
- File Name: haytararutyun.doc (statement.doc)
- SHA-256 Hash: fa406c532ea3d7cae05411df0ed5a541630a07f26a247a22d907f424397c72ce
- Delivery Method: The malware is delivered through a Word document (haytararutyun.doc) that contains a malicious VBA Macro code.
VBA Macro Functionality: The VBA Macro code within the document is intended to perform the following actions:
- Download a file (ekeng-mta.exe) from a remote server (hxxps[://]karabakhtelekom[.]com/api/ekeng-mta[.]exe).
- Execute the downloaded file using the command cmd /c C:\users\Public\Downloads\ekeng-mta.exe.
- Copy a file (Server.bat) to a different location.
- Run Server.bat with the vbHide attribute, potentially executing malicious code.
- Contact a remote Command and Control (C2) server (139.84.231.199) using PowerShell.
- Utilize encoded commands to bypass protection systems.
- Download additional files, including mta.ps1 and mta.dll, which are associated with the UrbanBishop payload.
UrbanBishop Payload:
- The malware includes a payload known as UrbanBishop, which is used for shellcode execution.
- UrbanBishop is a potentially open-source tool for Remote Access and Trojan (RAT) functionality.
Indicators of Compromise (IOCs)
Malicious Files:
haytararutyun.doc
- SHA-256 Hash:fa406c532ea3d7cae05411df0ed5a541630a07f26a247a22d907f424397c72ce
ekeng-mta.exe
- SHA-256 Hash: 3a679cb98f88d7d6bd84dcfe9717238c08c05942055bdb798103224e7f2f2ca9
mta.ps1
- SHA-256 Hash: 60416198c9b2105c9204638fd00e154e2f5c32ba45f5a8ae2671bae565c062e9
mta.dll
- SHA-256 Hash: be4bf8ae8ad02363ec3a3a0a932a439eab48c9427375038d121421806be32051
C2 Server:
- IP Address: 139.84.231.199
- Location: South Africa (a VPS server)
- IP Address: 193.161.193.99
- Location: Russia ( Hosting provider )
Domain:
- Domain Name: karabakhtelekom.com
- Registrar: eNom, LLC
- Creation Date: 2023-09-04
- Updated Date: 2023-09-11
- Currently on clientHold status, likely suspended.
Mitigation Strategies
Monitor Outgoing Connections:
- Implement monitoring of outgoing connections with PowerShell user-agent strings.
Network Layer Restriction:
- Restrict access to the IP address 139.84.231.199 at the network layer.
Process Monitoring:
- Continuously monitor running child processes, especially mta.dll.
Hash Value Checking:
Check the hash values of critical files:
- mta.ps1 (SHA-256: 72EF210030F0F470433A6AACC66DFBE4CBFDAD5C)
- mta.dll (SHA-256: F5145EC20482B39B727E980169DA92E36D4C5A6E)
Email Gateway Protection:
- Block emails originating from the domain aacpress.net to prevent further attacks.
Conclusion
This threat analysis report outlines a malware campaign targeting Armenians using a malicious MS Word document with embedded VBA Macro code. The malware’s functionalities include downloading and executing malicious payloads, contacting a remote C2 server, and utilizing the UrbanBishop payload. Mitigation strategies are provided to safeguard against this threat, emphasizing the importance of proactive monitoring and network security measures. Security teams are encouraged to stay vigilant and update their defenses accordingly.