A threat actor (TA) is currently engaged in a phishing campaign on Signal aimed at hijacking user accounts. The attack vector is social engineering, not a technical vulnerability within the Signal protocol or application. The TA impersonates “Signal Support” to manipulate targets into divulging their 6-digit registration verification code. Successful execution allows for account takeover only if the target’s Registration Lock is disabled.
Attack Analysis & TTPs
The attack follows a clear, multi-step process (Tactics, Techniques, and Procedures):
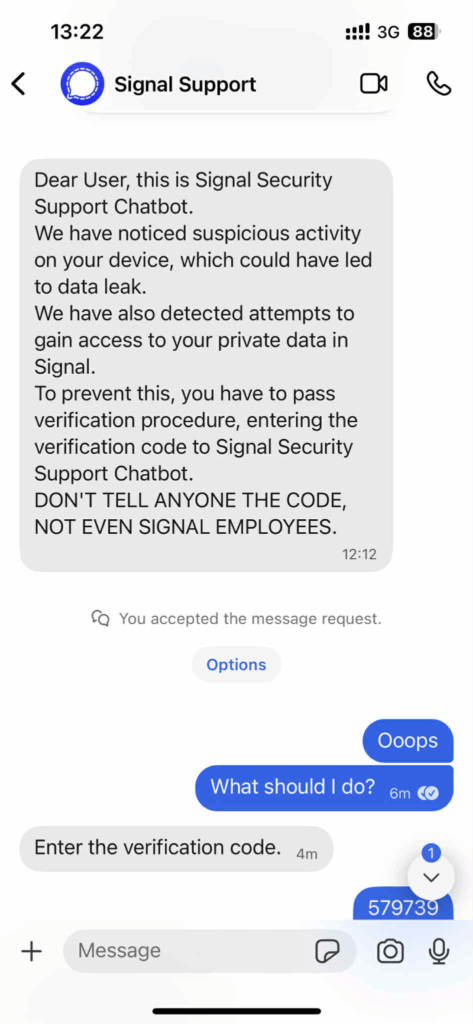
- Initial Contact (T1566.002 – Spearphishing Link/Message): The target receives a message from an unknown number with the profile name “Signal Support” or a variation thereof. The message, as observed, claims detection of “suspicious activity” to create urgency.
- Social Engineering (T1598 – Phishing for Information): The core of the attack is manipulating the user. The TA instructs the target to expect a verification code. Simultaneously, the TA initiates the Signal registration process for the target’s phone number on a TA-controlled device. This action triggers Signal’s legitimate backend to send a valid 6-digit one-time password (OTP) to the target’s device.
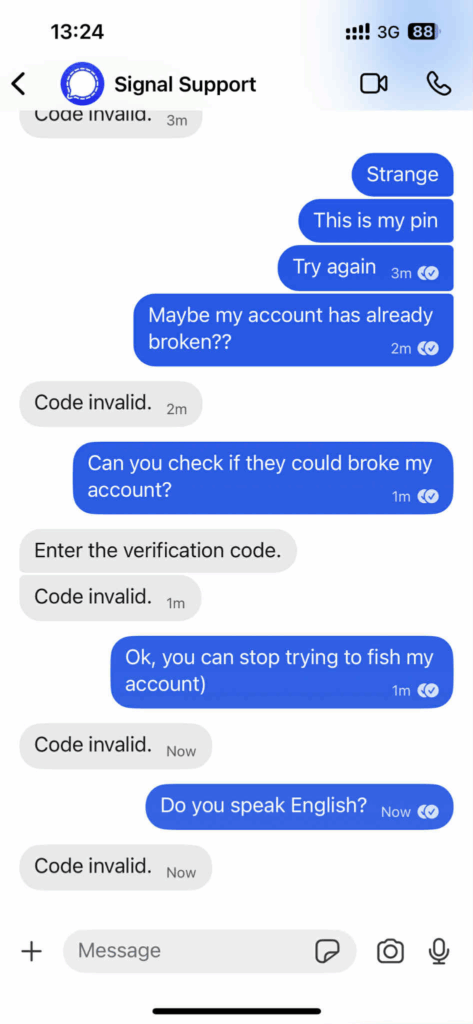
- Credential Harvesting: The TA then requests the target to provide this OTP in the chat. Our analysis, involving the submission of deliberately invalid codes, showed the TA’s process is likely manual or scripted. The TA’s response was a simple loop, repeatedly stating the code was “Invalid” and requesting the correct one.
- Reliance on Disabled Registration Lock: The absence of a request for the Registration Lock PIN highlights the TA’s dependency on targets having this crucial security feature disabled. If Registration Lock is active, an OTP alone is insufficient to complete the account takeover, as the PIN would still be required.
 |
|
Indicators & Detection
Detection relies on identifying the following red flags:
- Source: Unsolicited message from an entity claiming to be “Signal Support.” Signal does not initiate support contact via direct message.
- Content: Any message requesting a registration code. These are user-only secrets for the registration flow.
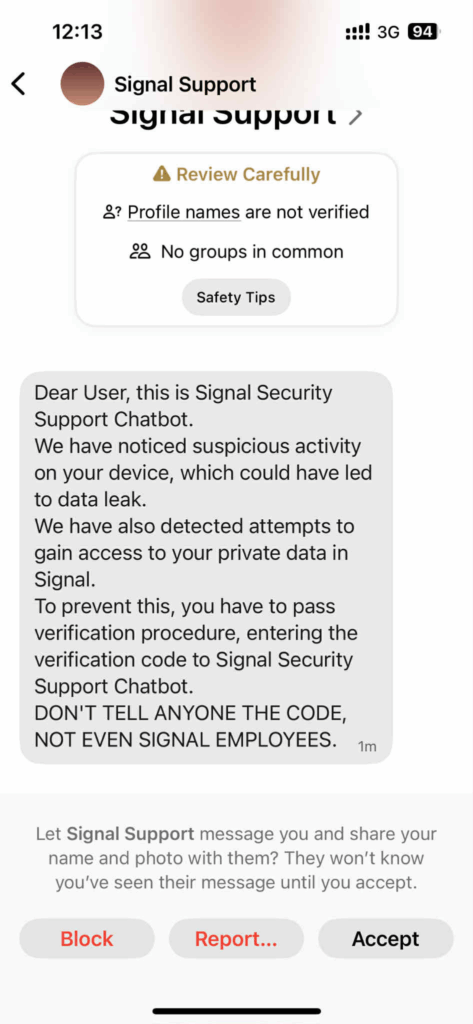
- Signal App Warnings: The app itself flags messages from unknown contacts where profile names are unverified and there is no shared group history. These warnings should be treated as high-priority alerts.
Mitigation and Hardening
This attack vector is rendered ineffective by proper account configuration.
-
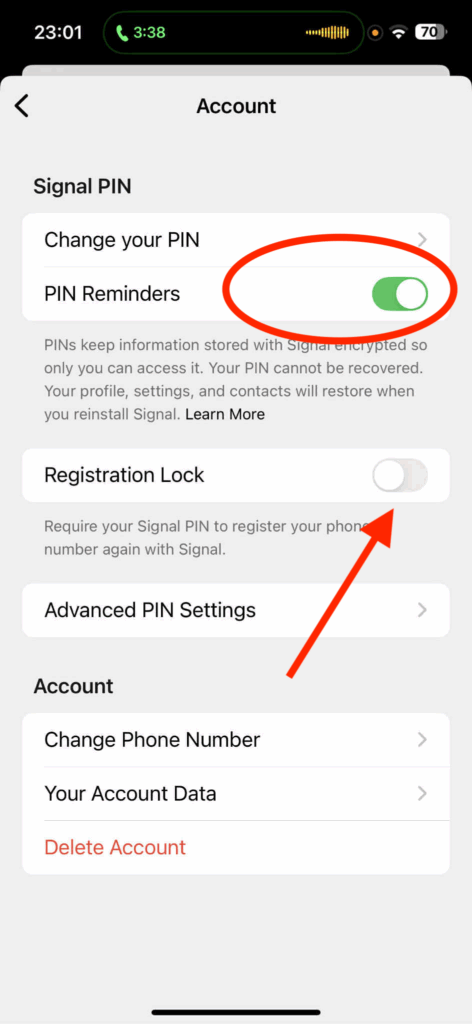 Primary Countermeasure: Registration Lock This is the most critical defense. Enabling Registration Lock requires a user-created PIN to be entered upon re-registering a phone number. This prevents an attacker with a valid OTP from completing the account takeover.
Primary Countermeasure: Registration Lock This is the most critical defense. Enabling Registration Lock requires a user-created PIN to be entered upon re-registering a phone number. This prevents an attacker with a valid OTP from completing the account takeover.
- Path:
Signal Settings > Account > Registration Lock > Enable
- Path:
- User Awareness:
- Treat all registration codes/OTPs as sensitive credentials. They are for user input into the app only, never for disclosure to a third party.
- Apply zero-trust principles to unsolicited inbound communications, regardless of the displayed sender name.
Incident Response
- If Targeted: Do not engage. Use the in-app
BlockandReportfunctions immediately. - If OTP is Compromised (Registration Lock Disabled): The account is vulnerable. The user must immediately re-register their own Signal instance on their primary device. This invalidates the attacker’s active registration session. After regaining control, enable Registration Lock immediately.
- If OTP is Compromised (Registration Lock Enabled): You are likely safe. The attacker cannot complete the takeover without the PIN. Block and report the sender.
- If you have shared the OTP and the attacker successfully registered (i.e., Registration Lock was disabled) and then changed your PIN: Your account has been compromised. The attacker can change your PIN and lock you out.
- Attempt to re-register your account immediately. If the attacker has not yet changed your PIN, you may be able to regain control.
- If you are locked out, you must alert your contacts through other means (email, another messaging app, phone call) that your Signal account has been compromised and that they should not trust any messages coming from it.
- Contact Signal’s official support team through their website for further guidance.