On May 28, 2025, CyberHUB-AM identified a sophisticated phishing attack targeting one of its NGO partners.
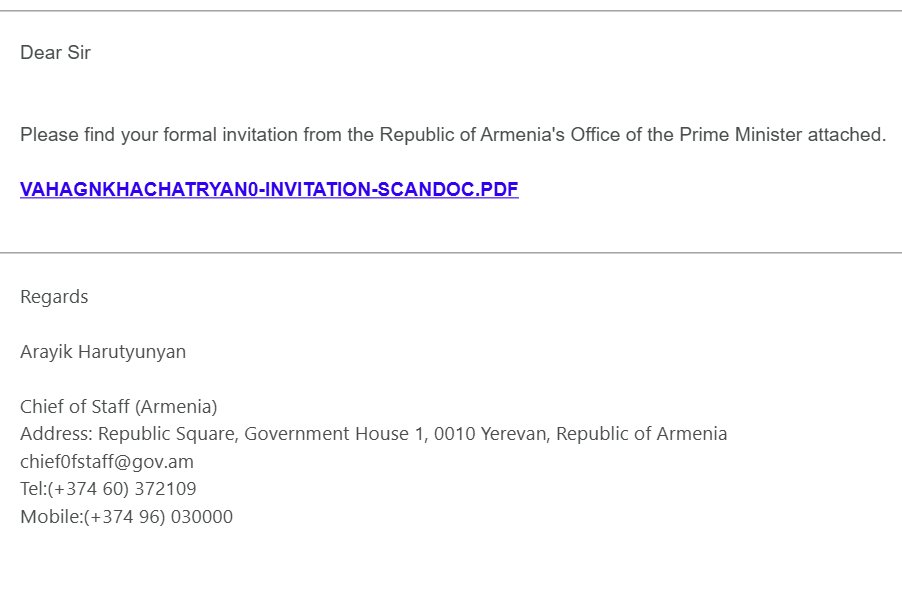
The attacker sent a phishing email with a PDF attachment link disguised as an official document—VAHAGNKHACHATRYAN0-INVITATION-SCANDOC.PDF. The URL hxxps[://]snip[.]ly/l9xqzf redirected to a malicious GitHub Pages site (hxxps[://]asw910[.]github[.]io/ar[.]mernia[.]github[.]io/index[.]html) crafted to mimic legitimate content. Embedded JavaScript within the page (jquery.min.js) initiated a credential harvesting routine, forwarding credentials to a compromised endpoint:hxxps[://]wbbuffetchurrascobh[.]com[.]br/wp-admin/email[.]php.

Target
The attack was explicitly aimed at civil society—specifically an Armenian NGO—demonstrating the threat actors’ strategic interest in advocacy organizations and regional politics.
Tactics, Techniques, and Procedures (TTPs)
Reconnaissance
-
Target Profiling: The phishing lure was customized with Armenian president Vahagn Khachaturyan’s name (
VAHAGN KHACHATRYAN), it came on behalf of Prime Minister’s Cheif of Staff, indicating prior knowledge or research.
Resource Development
-
Infrastructure Use:
-
GitHub user
asw910(newly created) hosted the payload on GitHub Pages. -
Redirect chain employed Snip.ly to mask the final malicious domain.
-
Delivery
-
Phishing Email: Delivered via standard email channels, containing a socially engineered link to trigger curiosity and urgency—hallmarks of spear phishing.
Credential Access
-
Credential Harvesting: Malicious JavaScript on the GitHub page captured submitted credentials and exfiltrated them using a POST request to a hijacked WordPress backend.
Obfuscation
-
Code Masquerading: The phishing payload masqueraded as a common JavaScript library (
jquery.min.js) to evade detection.
MITRE ATT&CK Mapping
-
T1566.001 – Phishing: Spearphishing Attachment
-
T1584 – Compromise Infrastructure
-
T1204.002 – User Execution: Malicious File
-
T1056.001 – Input Capture: Keylogging (via credential form capture)
-
T1071.001 – Application Layer Protocol: Web Protocols
Lessons Learned
-
Malicious Use of Reputable Infrastructure
Hosting malicious content on GitHub and using a known link shortener (Snip.ly) demonstrates how attackers exploit trusted services to improve click-through rates and bypass filters. -
Targeted Civil Society Attacks
The attack was not random. It reflects growing trends where politically motivated actors focus on NGOs, journalists, and activists, aligning with patterns described in various regional threat reports. -
Credential Capture via POST
This common but effective technique underlines the importance of inspecting outbound POST traffic for anomalies, especially to foreign domains or unrecognized endpoints. -
Defensive Gaps
Absence of URL filtering or user training enabled the victim to follow the malicious link. Organizations must prioritize layered security, including endpoint protection and DNS-based filtering.
Recommendations
-
Implement Domain-based Message Authentication (SPF, DKIM, DMARC)
To detect spoofed emails more effectively. -
Block Access to URL Shorteners
Unless whitelisted, to reduce click-through on potentially obfuscated URLs. -
Monitor GitHub and similar repositories for lookalike domains
As attackers increasingly abuse developer platforms to serve payloads. -
Conduct Regular Phishing Simulations and Awareness Training
Tailor campaigns to mimic current threat actor techniques.x