Security researcher Simon Kenin has documented a specific type of cyberattack known as “Pastejacking,” targeting Armenia. The attack is using the context of the recent political protests in the country and the name of the leader of the opposition protests Bagrat Galstanyan, a cleric of the Armenian Apostolic Church.
The researcher has found a word document written in Armenian which contains a link at the bottom:
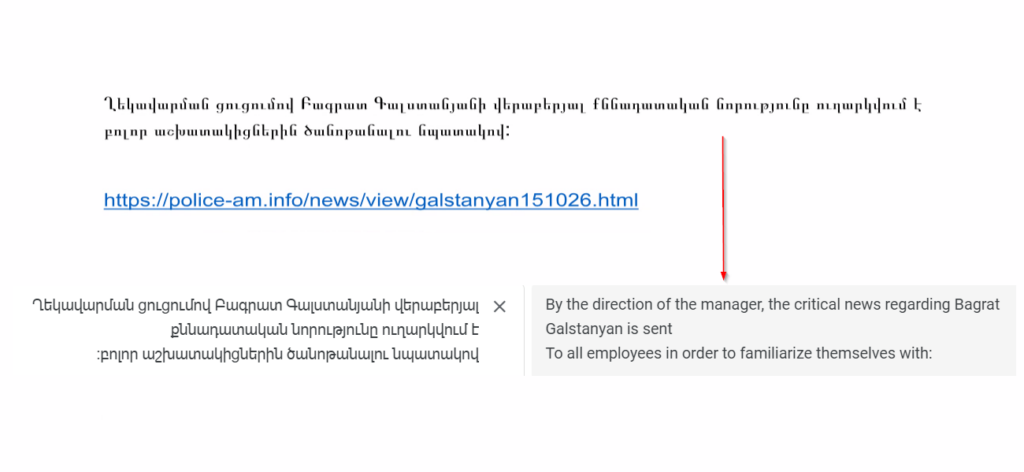
The link leads to a domain registered to look like the legitimate domain of the Armenian police. The domain has been registered this month — on 7th October, 2024, and is currently on-hold, apparently for being flagged as a phishing site. VirusTotal has some details, including some text scraped from the site, while it was still up and clearly showing keywords related to the Armenian Police.
Simon’s blog-post is more helpful here as well. According to the researcher, opening the link used to lead to a captcha message in Armenian, which itself leads to the pastejacking attack itself.
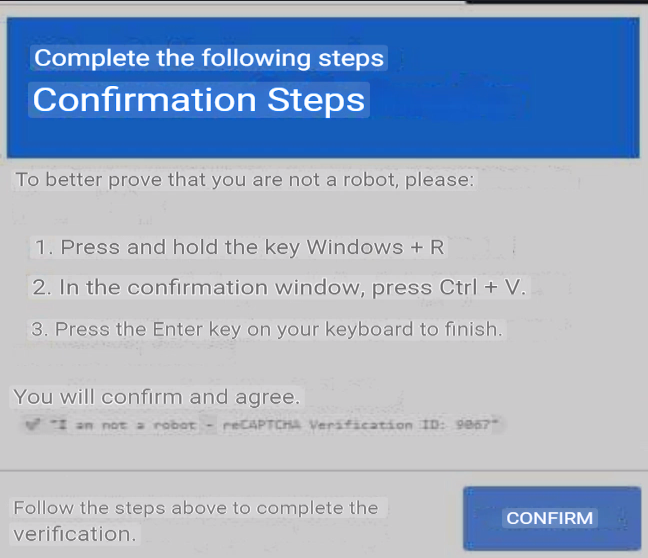
For the further details of the attack check out this link: https://k3yp0d.blogspot.com/2024/10/something-phishy-is-happening-in-armenia.html?lr=1730206198313.
We will further concentrate on what is this type of attack and how to protect from it.
What is Pastejacking?
Pastejacking is a cyberattack technique where attackers manipulate the content copied to a user’s clipboard. When a user copies text from a malicious website, the clipboard content is replaced with something different, often harmful. This can lead to unintended actions when the user pastes the content elsewhere, such as in a terminal or a document.
For example, a user might copy a seemingly harmless URL or command from a website, but when they paste it, the content has been altered to execute a malicious command or redirect to a phishing site. This can result in unauthorized access, data breaches, or the installation of malware.
How Pastejacking Works
- Clipboard Manipulation: Attackers use JavaScript to alter the clipboard content when a user copies text from a webpage. This script can replace the copied text with malicious commands or links.
- Execution of Malicious Commands: When the user pastes the altered content into a terminal or command prompt, the malicious command is executed, potentially compromising the system.
- Phishing and Redirection: The altered clipboard content can also redirect users to phishing sites, where attackers can steal sensitive information like login credentials.
Recommendations to Protect Against Pastejacking
- Be Cautious with Copying: Avoid copying text from untrusted websites. If you must copy text, verify the content before pasting it.
- Verify Pasted Content: Always double-check the content you paste, especially in sensitive environments like terminals or command prompts.
- Educate and Train: Raise awareness about Pastejacking among employees and provide training on safe browsing practices.
By staying vigilant and adopting these protective measures, you can significantly reduce the risk of falling victim to Pastejacking attacks.