CyberHUB-AM has been contacted by a senior editor from an Armenian media outlet who had received what appeared to be an urgent security notification on Signal. The message claimed that a new device had been linked to the editor’s account from abroad and urged immediate action to “cancel” the connection.
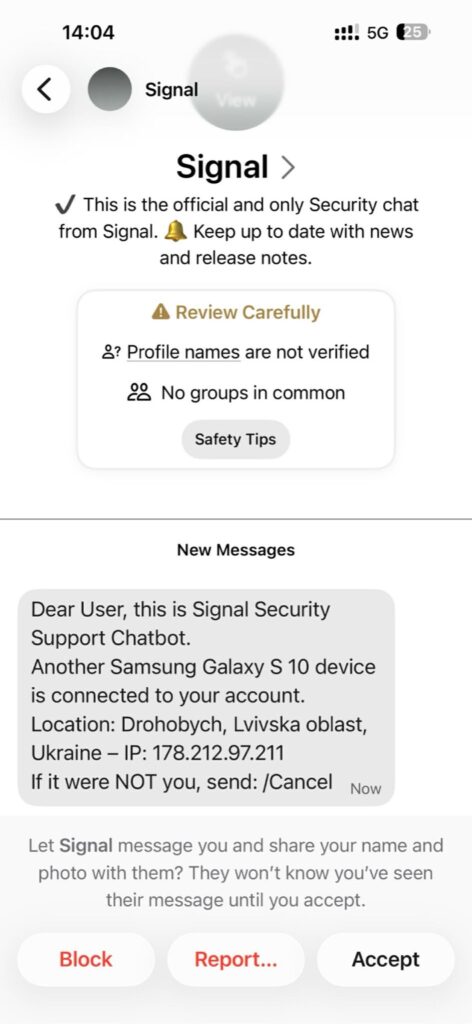
At first glance, the message was designed to look authoritative and time-sensitive. It presented itself as coming from a “Signal Security Support Chatbot” and included a specific device model, a geographic location in Ukraine, and an IP address. The implication was clear: someone had accessed the account, and the user needed to act fast.
In reality, the message was a phishing attempt.
What makes this incident particularly concerning is that the recipient was not randomly selected.
The editor has been repeatedly targeted in the past by Signal-related phishing messages and has also previously been identified as a target of mercenary spyware.
In that context, this message appears less like an isolated scam and more like another step in a long-running pattern of targeted digital harassment and surveillance.
The content of the message itself reveals several red flags. Signal does not operate security support chatbots that initiate conversations with users. It does not notify users of account activity through unsolicited private messages, nor does it expose IP addresses or geolocation data in this manner. The instruction to reply with a command—“/Cancel”—is a classic social engineering technique, intended to provoke engagement and open the door to further manipulation.
Signal’s own interface quietly warned that something was wrong. The chat was marked with notices indicating that the sender’s profile was not verified and that there were no shared groups—subtle but important indicators that the message did not come from a trusted source.
For journalists and editors, these kinds of messages are rarely just about one click or one reply. They often serve as reconnaissance, testing how a target reacts, whether they engage, and what information might be extracted next. In more serious cases, phishing is used to prepare the ground for account takeover or spyware infection, especially when the target has already been singled out in the past.
This case is a reminder that secure messaging platforms are increasingly being used as attack surfaces rather than safe havens. The trust users place in tools like Signal is precisely what makes them attractive to attackers, particularly when targeting media professionals, civil society actors, and public figures.
CyberHUB-AM encourages journalists and media organizations to treat unexpected “security alerts” on messaging platforms with skepticism, even when they appear technically detailed or urgent. Reviewing linked devices directly in the app, refusing to interact with unsolicited messages, and reporting suspicious contacts remain essential defensive habits.
We will continue to document and analyze targeted digital attacks against Armenian journalists and editors. If you or your organization encounter similar incidents, CyberHUB-AM welcomes secure reports through our usual channels.