This report details a social engineering and phishing campaign targeting Armenian Facebook users. The attackers impersonate major local supermarket chains—specifically Yerevan City and Carrefour—to lure victims into fraudulent schemes under the guise of a Christmas giveaway.
1. Attack Vector and Initial Lure
-
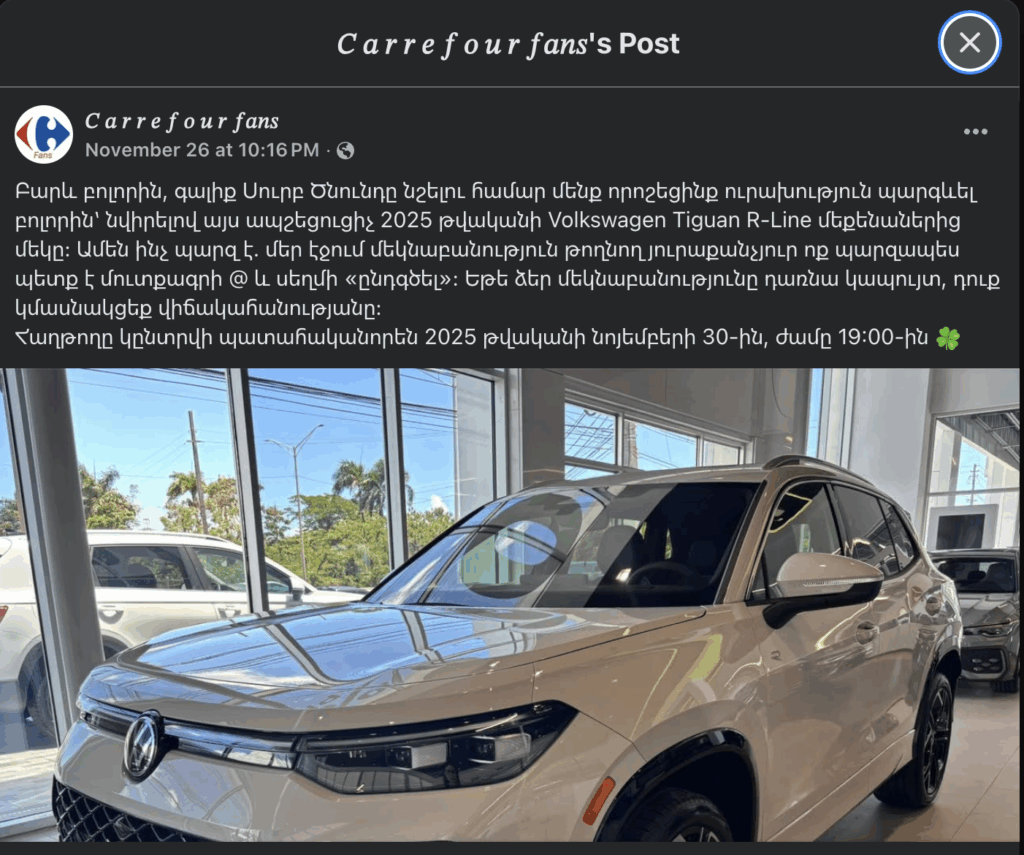
Impersonation: The attackers utilize fake Facebook profiles to establish credibility. Identified profiles include “yerevan City.” and “Carrefour fans”.
-
The Lure: The fraudulent posts claim that to celebrate the upcoming Christmas holiday, the supermarkets are gifting 2025 Volkswagen Tiguan R-Line vehicles to lucky winners.
-
Engagement Mechanism: Users are instructed to comment on the post by typing “@” and clicking “highlight” to enter the raffle. The posts claim winners will be chosen randomly on November 30, 2025.
2. Social Engineering and Automation
Once a victim engages with the post, the attack moves to direct messaging, likely utilizing automated chatbots.
-
False Notification: Victims receive immediate messages stating they have been officially selected as a winner.
-
Persona Use: The messages often appear to come from a specific persona named “Artur Papyan” or simply the brand page.
-
Urgency Tactics: The scammers create false urgency, telling victims they have limited time (e.g., 10 minutes) to register and claim the prize before it is given to another participant.
-
Instructions: Victims are asked to click a link to “register” their name on a website and send a screenshot of the confirmation.
3. Technical Analysis and Exploitation
The campaign utilizes a complex chain of redirects to filter users and deliver different payloads based on their device or operating system.
A. Phishing and Data Theft
-
Landing Pages: Users are redirected to intermediary sites, such as Blogspot domains (e.g.,
mnhgdfcbvghdhfghhhhng.blogspot.com). -
Financial Fraud: The fake registration page mimics the supermarket branding (showing logos for “Biella,” “GOLD,” etc.) and asks for credit card details. The site claims the card is needed only for identity verification and that the process is “100% free”.
B. Redirect Chain The attack utilizes URL shorteners and API calls to obfuscate the final destination:
-
Initial Links:
tinyurl.com/3a44vd8uandbotcake.iolinks are used in the chat messages. -
Intermediate Redirects: Traffic is routed through domains like
kanatsarsenbek.comandd.kissenchachen.top.
C. Device-Specific Payloads The campaign behavior changes based on the victim’s operating system:
-
SMS Fraud (Android/Mobile): On some test devices, the site attempted to force the user to send an SMS verification message to a specific number (
+201192811290) with a specific body text (Мой доступ готов...), likely subscribing the user to premium-rate services. -
Malicious Software/Adware (iOS/Mobile): On other devices, users were redirected to download pages for “Mix VPN” or “Super Proxy Master”. The user is prompted to install the app to “continue watching in a safe mode” or claim a bonus.
4. Indicators of Compromise (IOCs)
Facebook Profile IDs:
-
61583716291738 -
61584021944867
Malicious Domains & URLs:
-
tinyurl.com/3a44vd8u -
mnhgdfcbvghdhfghhhhng.blogspot.com -
kanatsarsenbek.com -
d.kissenchachen.top -
botcake.io